spectre_meltdown_checker をかけてみた(32bit版)
最新カーネルでも、全て Vulnerable になりました。
いやなら、64bit に鞍替えしろ、ということみたいですね。
CentOS 7系 で firewalld ではなく iptables を使う
CentOS 7系では、firewalld がデフォルトですが、iptables を使うこともできます。
以下、手順となります。
1. iptables-services パッケージをインストールする
# yum install iptables-services
ls -la /etc/sysconfig/iptables
設定ファイルが、既にファイル化されていました。
2. firewalld が吐いたポリシを、iptables のポリシに変換する
# iptables -S | tee ~/firewalld_iptables_rules
# ip6tables -S | tee ~/firewalld_ip6tables_rules
以下のようなコマンドで、firewalld のポリシを /etc/sysconfig/iptables にコピペできるようになると思います。これでひっかからないものでも、作成したものを忘れずにコピーしましょう。
grep 'ACCEPT\|DROP\|QUEUE\|RETURN\|REJECT\|LOG' ~/firewalld_iptables_rules > firewalld_iptables_rules_x
適宜、firewalld のポリシルールを /etc/sysconfig/iptables にコピーします。
3. サービス起動の設定
firewalld が立ち上がらないようにして、iptables が立ち上がるようにしましょう。
# systemctl disable firewalld.service
# systemctl mask firewalld.service
# systemctl enable iptables.service
システム再起動
4. 調整
# systemctl status iptables.service
うまく立ち上がっていなかったら、ログを見て、調整してください。
たぶん、firewalld 特有の設定をコピーしているのかもしれませんので、適宜直してください。
spectre_meltdown_checker をかけてみた(最新版)
表示が詳しくなって、対策が進んでいる事がわかります。
CPU には脆弱性があるが、kernel の Mitigation でなんとかこらえている感じか。。
# ./spectre_meltdown_checker.sh
Spectre and Meltdown mitigation detection tool v0.34+
Checking for vulnerabilities on current system
Kernel is Linux 4.14.14-300.fc27.x86_64 #1 SMP Fri Jan 19 13:19:54 UTC 2018 x86_64
CPU is Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz
Hardware check
* Hardware support (CPU microcode) for mitigation techniques
* Indirect Branch Restricted Speculation (IBRS)
* SPEC_CTRL MSR is available: YES
* CPU indicates IBRS capability: YES (SPEC_CTRL feature bit)
* Indirect Branch Prediction Barrier (IBPB)
* PRED_CMD MSR is available: YES
* CPU indicates IBPB capability: YES (SPEC_CTRL feature bit)
* Single Thread Indirect Branch Predictors (STIBP)
* SPEC_CTRL MSR is available: YES
* CPU indicates STIBP capability: YES
* Enhanced IBRS (IBRS_ALL)
* CPU indicates ARCH_CAPABILITIES MSR availability: NO
* ARCH_CAPABILITIES MSR advertises IBRS_ALL capability: NO
* CPU explicitly indicates not being vulnerable to Meltdown (RDCL_NO): NO
* CPU microcode is known to cause stability problems: YES (model 94 stepping 3 ucode 0xc2)
The microcode your CPU is running on is known to cause instability problems,
such as intempestive reboots or random crashes.
You are advised to either revert to a previous microcode version (that might not have
the mitigations for Spectre), or upgrade to a newer one if available.
* CPU vulnerability to the three speculative execution attacks variants
* Vulnerable to Variant 1: YES
* Vulnerable to Variant 2: YES
* Vulnerable to Variant 3: YES
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Mitigated according to the /sys interface: NO (kernel confirms your system is vulnerable)
* Kernel has array_index_mask_nospec: NO
* Checking count of LFENCE instructions following a jump in kernel: NO (only 5 jump-then-lfence instructions found, should be >= 30 (heuristic))
> STATUS: VULNERABLE (Kernel source needs to be patched to mitigate the vulnerability)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Mitigated according to the /sys interface: YES (kernel confirms that the mitigation is active)
* Mitigation 1
* Kernel is compiled with IBRS/IBPB support: NO
* Currently enabled features
* IBRS enabled for Kernel space: NO
* IBRS enabled for User space: NO
* IBPB enabled: NO
* Mitigation 2
* Kernel compiled with retpoline option: YES
* Kernel compiled with a retpoline-aware compiler: YES (kernel reports full retpoline compilation)
* Retpoline enabled: YES
> STATUS: NOT VULNERABLE (Mitigation: Full generic retpoline)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Mitigated according to the /sys interface: YES (kernel confirms that the mitigation is active)
* Kernel supports Page Table Isolation (PTI): YES
* PTI enabled and active: YES
* Running as a Xen PV DomU: NO
> STATUS: NOT VULNERABLE (Mitigation: PTI)
A false sense of security is worse than no security at all, see --disclaimer
Spectre 対策の進捗について
急いては事を仕損じる、と。fedoramagazine.org
spectre_meltdown_checker をかけてみた
ノートPC
# ./spectre_meltdown_checker.sh
Spectre and Meltdown mitigation detection tool v0.31
Checking for vulnerabilities against running kernel Linux 4.14.13-300.fc27.x86_64 #1 SMP Thu Jan 11 04:00:01 UTC 2018 x86_64
CPU is Intel(R) Core(TM) i7-6700HQ CPU @ 2.60GHz
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Checking whether we're safe according to the /sys interface: NO (kernel confirms your system is vulnerable)
> STATUS: VULNERABLE (Vulnerable)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Checking whether we're safe according to the /sys interface: NO (kernel confirms your system is vulnerable)
> STATUS: VULNERABLE (Vulnerable: Minimal generic ASM retpoline)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Checking whether we're safe according to the /sys interface: YES (kernel confirms that the mitigation is active)
> STATUS: NOT VULNERABLE (Mitigation: PTI)
A false sense of security is worse than no security at all, see --disclaimer
------------------------
AWS の貧弱なサーバ
# ./spectre_meltdown_checker.sh
Spectre and Meltdown mitigation detection tool v0.31
Checking for vulnerabilities against running kernel Linux 4.14.11-300.fc27.x86_64 #1 SMP Wed Jan 3 13:52:28 UTC 2018 x86_64
CPU is Intel(R) Xeon(R) CPU E5-2670 v2 @ 2.50GHz
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Checking count of LFENCE opcodes in kernel: NO
> STATUS: VULNERABLE (only 25 opcodes found, should be >= 70, heuristic to be improved when official patches become available)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Mitigation 1
* Hardware (CPU microcode) support for mitigation
* The SPEC_CTRL MSR is available: YES
* The SPEC_CTRL CPUID feature bit is set: NO
* Kernel support for IBRS: NO
* IBRS enabled for Kernel space: NO
* IBRS enabled for User space: NO
* Mitigation 2
* Kernel compiled with retpoline option: NO
* Kernel compiled with a retpoline-aware compiler: NO
> STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): YES
* PTI enabled and active: YES
* Checking if we're running under Xen PV (64 bits): NO
> STATUS: NOT VULNERABLE (PTI mitigates the vulnerability)
A false sense of security is worse than no security at all, see --disclaimer
--------
古いカーネルでやってみた。
$ ./spectre_meltdown_checker.sh
Spectre and Meltdown mitigation detection tool v0.31
Note that you should launch this script with root privileges to get accurate information.
We'll proceed but you might see permission denied errors.
To run it as root, you can try the following command: sudo ./spectre_meltdown_checker.sh
Checking for vulnerabilities against running kernel Linux 4.14.8-300.fc27.x86_64 #1 SMP Wed Dec 20 19:00:18 UTC 2017 x86_64
CPU is Intel(R) Core(TM) i7-3630QM CPU @ 2.40GHz
CVE-2017-5753 [bounds check bypass] aka 'Spectre Variant 1'
* Checking count of LFENCE opcodes in kernel: NO
> STATUS: VULNERABLE (only 25 opcodes found, should be >= 70, heuristic to be improved when official patches become available)
CVE-2017-5715 [branch target injection] aka 'Spectre Variant 2'
* Mitigation 1
* Hardware (CPU microcode) support for mitigation
* The SPEC_CTRL MSR is available: NO
* The SPEC_CTRL CPUID feature bit is set: NO
* Kernel support for IBRS: NO
* IBRS enabled for Kernel space: NO
* IBRS enabled for User space: NO
* Mitigation 2
* Kernel compiled with retpoline option: NO
* Kernel compiled with a retpoline-aware compiler: NO
> STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): NO
* PTI enabled and active: NO
* Checking if we're running under Xen PV (64 bits): NO
> STATUS: VULNERABLE (PTI is needed to mitigate the vulnerability)
A false sense of security is worse than no security at all, see --disclaimer
spectre の点検
https://gist.github.com/intrajp/ae240cc69b37537957eadb29103bd9be
[ae240cc69b37537957eadb29103bd9be-a7ac31bcd12657a3d8dfa868b4c23e39ee68b137]$ ./spectre
Reading 40 bytes:
Reading at malicious_x = 0xffffffffffdffac0... Unclear: 0x54=’T’ score=976 (second best: 0x01 score=806)
Reading at malicious_x = 0xffffffffffdffac1... Unclear: 0x68=’h’ score=999 (second best: 0x01 score=778)
Reading at malicious_x = 0xffffffffffdffac2... Unclear: 0x65=’e’ score=998 (second best: 0x01 score=803)
Reading at malicious_x = 0xffffffffffdffac3... Unclear: 0x20=’ ’ score=999 (second best: 0x01 score=811)
Reading at malicious_x = 0xffffffffffdffac4... Unclear: 0x4D=’M’ score=999 (second best: 0x01 score=818)
Reading at malicious_x = 0xffffffffffdffac5... Unclear: 0x61=’a’ score=999 (second best: 0x01 score=823)
Reading at malicious_x = 0xffffffffffdffac6... Unclear: 0x67=’g’ score=999 (second best: 0x01 score=802)
Reading at malicious_x = 0xffffffffffdffac7... Unclear: 0x69=’i’ score=999 (second best: 0x01 score=825)
Reading at malicious_x = 0xffffffffffdffac8... Unclear: 0x63=’c’ score=999 (second best: 0x01 score=808)
Reading at malicious_x = 0xffffffffffdffac9... Unclear: 0x20=’ ’ score=999 (second best: 0x01 score=833)
Reading at malicious_x = 0xffffffffffdffaca... Unclear: 0x57=’W’ score=998 (second best: 0x01 score=792)
Reading at malicious_x = 0xffffffffffdffacb... Unclear: 0x6F=’o’ score=999 (second best: 0x01 score=793)
Reading at malicious_x = 0xffffffffffdffacc... Unclear: 0x72=’r’ score=999 (second best: 0x01 score=789)
Reading at malicious_x = 0xffffffffffdffacd... Unclear: 0x64=’d’ score=999 (second best: 0x01 score=824)
Reading at malicious_x = 0xffffffffffdfface... Unclear: 0x73=’s’ score=999 (second best: 0x01 score=769)
Reading at malicious_x = 0xffffffffffdffacf... Unclear: 0x20=’ ’ score=999 (second best: 0x01 score=812)
Reading at malicious_x = 0xffffffffffdffad0... Unclear: 0x61=’a’ score=999 (second best: 0x01 score=810)
Reading at malicious_x = 0xffffffffffdffad1... Unclear: 0x72=’r’ score=999 (second best: 0x01 score=792)
Reading at malicious_x = 0xffffffffffdffad2... Unclear: 0x65=’e’ score=998 (second best: 0x01 score=799)
Reading at malicious_x = 0xffffffffffdffad3... Unclear: 0x20=’ ’ score=999 (second best: 0x01 score=802)
Reading at malicious_x = 0xffffffffffdffad4... Unclear: 0x53=’S’ score=999 (second best: 0x01 score=793)
Reading at malicious_x = 0xffffffffffdffad5... Unclear: 0x71=’q’ score=998 (second best: 0x01 score=809)
Reading at malicious_x = 0xffffffffffdffad6... Unclear: 0x75=’u’ score=999 (second best: 0x01 score=824)
Reading at malicious_x = 0xffffffffffdffad7... Unclear: 0x65=’e’ score=999 (second best: 0x01 score=819)
Reading at malicious_x = 0xffffffffffdffad8... Unclear: 0x61=’a’ score=999 (second best: 0x01 score=801)
Reading at malicious_x = 0xffffffffffdffad9... Unclear: 0x6D=’m’ score=999 (second best: 0x01 score=783)
Reading at malicious_x = 0xffffffffffdffada... Unclear: 0x69=’i’ score=999 (second best: 0x01 score=821)
Reading at malicious_x = 0xffffffffffdffadb... Unclear: 0x73=’s’ score=999 (second best: 0x01 score=803)
Reading at malicious_x = 0xffffffffffdffadc... Unclear: 0x68=’h’ score=999 (second best: 0x01 score=801)
Reading at malicious_x = 0xffffffffffdffadd... Unclear: 0x20=’ ’ score=997 (second best: 0x01 score=832)
Reading at malicious_x = 0xffffffffffdffade... Unclear: 0x4F=’O’ score=999 (second best: 0x01 score=771)
Reading at malicious_x = 0xffffffffffdffadf... Unclear: 0x73=’s’ score=999 (second best: 0x01 score=818)
Reading at malicious_x = 0xffffffffffdffae0... Unclear: 0x73=’s’ score=999 (second best: 0x01 score=821)
Reading at malicious_x = 0xffffffffffdffae1... Unclear: 0x69=’i’ score=999 (second best: 0x01 score=837)
Reading at malicious_x = 0xffffffffffdffae2... Unclear: 0x66=’f’ score=998 (second best: 0x01 score=770)
Reading at malicious_x = 0xffffffffffdffae3... Unclear: 0x72=’r’ score=998 (second best: 0x01 score=820)
Reading at malicious_x = 0xffffffffffdffae4... Unclear: 0x61=’a’ score=996 (second best: 0x01 score=795)
Reading at malicious_x = 0xffffffffffdffae5... Unclear: 0x67=’g’ score=986 (second best: 0x01 score=755)
Reading at malicious_x = 0xffffffffffdffae6... Unclear: 0x65=’e’ score=951 (second best: 0x01 score=760)
Reading at malicious_x = 0xffffffffffdffae7... Unclear: 0x2E=’.’ score=995 (second best: 0x01 score=802)
自分のサーバを自分で作った sar-analyzer で評価する
ということで、やってみました。
AWS の貧弱なマシンになります。
#### Report by sar-analyzer ####
-- Report of CPU utilization --
Highest Average value of '%usr(%user)' for CPU all is 21.07 (01/10/18)
Lowest Average value of '%usr(%user)' for CPU all is 0.02 (01/02/18)
Highest Average value of '%sys(%system)' for CPU all is 33.84 (01/10/18)
Lowest Average value of '%sys(%system)' for CPU all is 0.05 (01/02/18)
Highest Average value of '%iowait' for CPU all is 0.20 (01/10/18)
Lowest Average value of '%iowait' for CPU all is 0.05 (01/02/18)
Highest Average value of '%idle' for CPU all is 99.82 (01/02/18)
Lowest Average value of '%idle' for CPU all is 43.98 (01/10/18)
Highest Average value of '%usr(%user)' for CPU 0 is 21.07 (01/10/18)
Lowest Average value of '%usr(%user)' for CPU 0 is 0.02 (01/02/18)
Highest Average value of '%sys(%system)' for CPU 0 is 33.84 (01/10/18)
Lowest Average value of '%sys(%system)' for CPU 0 is 0.05 (01/02/18)
Highest Average value of '%iowait' for CPU 0 is 0.20 (01/10/18)
Lowest Average value of '%iowait' for CPU 0 is 0.05 (01/02/18)
Highest Average value of '%idle' for CPU 0 is 99.82 (01/02/18)
Lowest Average value of '%idle' for CPU 0 is 43.98 (01/10/18)
--------
Each CPU can be in one of four states: user, sys, idle, iowait.
If '%usr' is over 60%, applications are in a busy state. Check with ps command which application is busy.
If '%sys' is over '%usr', kernel is in a busy state. Check cswch is high or not.
If '%iowait' is high, cpu is working for other task more. Note that iowait sometimes meaningless, at all.
Check swap statistics or high disk I/O would be the cause. Also check process or memory statistics.
If %idle is lower than 30%, you would need new CPU or cores.
Check not only 'CPU all', but each CPU values. And if some of their values are high, check the sar file of that date.
-- Report of queue length and load averages --
Highest Average value of 'runq-sz' is 1 (12/30/17)
Lowest Average value of 'runq-sz' is 0 (01/01/18)
Highest Average value of 'plist-sz' is 357 (01/03/18)
Lowest Average value of 'plist-sz' is 293 (01/10/18)
Highest Average value of 'ldavg-1' is 0.56 (01/10/18)
Lowest Average value of 'ldavg-1' is 0.00 (01/01/18)
Highest Average value of 'ldavg-5' is 1.40 (01/10/18)
Lowest Average value of 'ldavg-5' is 0.00 (01/01/18)
Highest Average value of 'ldavg-15' is 0.77 (01/10/18)
Lowest Average value of 'ldavg-15' is 0.00 (01/01/18)
--------
If 'runq-sz' is over 2, the box is cpu bound.
If that is the case, you might need more cpu power to do the task.
If 'plist-sz' is higher than 10,000 for example, there are waits.
If 'ldavg-<minites>' exceeds number of cores, cpu load is high.
Check number of cores with, $cat /proc/cpuinfo | grep 'cpu cores'.
Check number of physical cpu with, $cat /proc/cpuinfo | grep 'pysical id'.
Check if hyperthreading is enabled with, $cat /proc/cpuinfo | grep 'siblings'.
Devide the result of above command and if it is not same as core, hyperthreading is enabled.
So, if you have 8 cores, highest value is 800.00 and above 70% of this value would be a trouble.
-- Report task creation and system switching activity --
Highest Average value of '%proc/s' is 758.82 (01/10/18)
Lowest Average value of '%proc/s' is 0.20 (01/02/18)
Highest Average value of '%cswch/s' is 10015.51 (01/10/18)
Lowest Average value of '%cswch/s' is 80.21 (01/06/18)
--------
proc/s shows number of tasks which was created per second.
Check the order. Depends on cores, but under 100 would be fine.
cswch/s shows number of context switching activity of CPU per second.
Check the order. Depends on cores, but under 10000 would be fine.
-- Report paging statistics --
Highest Average value of '%fault/s' is 48092.51 (01/10/18)
Lowest Average value of '%fault/s' is 86.95 (01/11/18)
Highest Average value of '%majflt/s' is 0.35 (01/10/18)
Lowest Average value of '%majflt/s' is 0.00 (01/01/18)
Highest Average value of '%vmeff/s' is 100.00 (01/12/18)
Lowest Average value of '%vmeff/s' is 0.00 (01/06/18)
--------
If fault/s is high, programs may requiring memory. Check with, say '# ps -o min_flt,maj_flt <PID>'.
If majflt/s is high, some big program had been started somehow on that day.
If vmeff/s is 0, no worry on memory, if vmeff/s is not 0 and over 90.00, it is good.
If vmeff/s is under 30.00, somethig is wrong.
-- Report memory utilization statistics --
Highest Average value of '%memused/s' is 85.49 (01/01/18)
Lowest Average value of '%memused/s' is 33.22 (01/10/18)
Highest Average value of 'kbcommit' is 2620525 (01/03/18)
Lowest Average value of 'kbcommit' is 2048996 (01/10/18)
Highest Average value of '%commit/s' is 258.92 (01/03/18)
Lowest Average value of '%commit/s' is 203.63 (01/10/18)
--------
Even if %memused is around 99.0%, it's OK with Linux.
Check the highest value of kbcommit. This amount of memory is needed for the system. If lacking, consider adding more memory.
If %commit is over 100%, memory shortage is occurring. Gain swap or add more memory.
-- Report I/O and transfer rate statistics --
Highest Average value of 'tps' is 5.70 (01/10/18)
Lowest Average value of 'tps' is 1.79 (01/11/18)
Highest Average value of 'bread/s' is 106.29 (01/10/18)
Lowest Average value of 'bread/s' is 0.04 (01/08/18)
Highest Average value of 'bwrtn/s' is 104.01 (01/10/18)
Lowest Average value of 'bwrtn/s' is 42.03 (01/06/18)
--------
tps is total number of transfers per second that were issued to physical devices.
A transfer is an I/O request to a physical device.
Multiple logical requests can be combined into a single I/O request to the device.
A transfer is of indeterminate size.
bread/s is Total amount of data read from the devices in blocks per second.
Blocks are equivalent to sectors and therefore have a size of 512 bytes.
bwrtn/s is Total amount of data written to devices in blocks per second.
If these values are, say over 10000 or some, I/O was heavy on that day. Chech the sar file related.
Check iowait on CPU, also.
-- Report activity for each block device --
Highest Average value of 'areq-sz' of dev202-0 is 18.44 (01/10/18)
Lowest Average value of 'areq-sz' of dev202-0 is 8.49 (01/01/18)
Highest Average value of '%util' of dev202-0 is 0.13 (01/10/18)
Lowest Average value of '%util' of dev202-0 is 0.05 (01/06/18)
--------
'areq-sz' is the average size (in kilobytes) of the I/O requests that were issued to the device.
Note: In previous versions, this field was known as avgrq-sz and was expressed in sectors.
'%util'is percentage of elapsed time during which I/O requests were issued to the device
(bandwidth utilization for the device). Device saturation occurs when this value
is close to 100% for devices serving requests serially. But for devices serving requests in
parallel, such as RAID arrays and modern SSDs, this number does not reflect their performance limits.
-- Report swap space utilization statistics --
Highest Average value of '%swpused' is 0.00 (01/01/18)
Lowest Average value of '%swpused' is 0.00 (01/01/18)
--------
%swpused percentage of used swap space.
If it's high, the system is memory bound.
--------
やっぱ、メモリ足りんかな。
sar-analyzer の開発状況
元気ですか?
sar-analyzer の開発ですが、結構進みました。DEVICE のところの仕組みができたので、これを皮切りに、ネットワークデバイスも解析できそうです。
いまでも結構便利だと思いますよ。日々の業務に役立ててみてください。
もう少し頑張ります。では。。
Meltdown 関連パッチ適用後のベンチマーク結果
カーネルをアップデートしてしまったのですが、どの程度の機能低下?が見られるようになったかを、知りたいです。
そこで、UnixBench をやってみることにしました。
まずは、最新カーネルのままで実行してみました。
# grubby --default-kernel
/boot/vmlinuz-4.14.11-300.fc27.x86_64
# grubby --default-index
0
# grubby --info=ALL
index=0
kernel=/boot/vmlinuz-4.14.11-300.fc27.x86_64
args="ro rd.lvm.lv=fedora/root rd.lvm.lv=fedora/swap nomodeset rhgb quiet LANG=ja_JP.UTF-8"
root=/dev/mapper/fedora-root
initrd=/boot/initramfs-4.14.11-300.fc27.x86_64.img
title=Fedora (4.14.11-300.fc27.x86_64) 27 (Twenty Seven)
index=1
kernel=/boot/vmlinuz-4.14.8-300.fc27.x86_64
args="ro rd.lvm.lv=fedora/root rd.lvm.lv=fedora/swap nomodeset rhgb quiet LANG=ja_JP.UTF-8"
root=/dev/mapper/fedora-root
initrd=/boot/initramfs-4.14.8-300.fc27.x86_64.img
title=Fedora (4.14.8-300.fc27.x86_64) 27 (Twenty Seven)
index=2
kernel=/boot/vmlinuz-4.14.7-300.fc27.x86_64
args="ro rd.lvm.lv=fedora/root rd.lvm.lv=fedora/swap nomodeset rhgb quiet LANG=ja_JP.UTF-8"
root=/dev/mapper/fedora-root
initrd=/boot/initramfs-4.14.7-300.fc27.x86_64.img
title=Fedora (4.14.7-300.fc27.x86_64) 27 (Twenty Seven)
index=3
kernel=/boot/vmlinuz-0-rescue-341f3defedb547699a016a1a9e6e6da8
args="ro rd.lvm.lv=fedora/root rd.lvm.lv=fedora/swap nomodeset rhgb quiet"
root=/dev/mapper/fedora-root
initrd=/boot/initramfs-0-rescue-341f3defedb547699a016a1a9e6e6da8.img
title=Fedora (0-rescue-341f3defedb547699a016a1a9e6e6da8) 25 (Twenty Five)
index=4
non linux entry
一つ前のカーネルに設定してみます。
# grubby --set-default /boot/vmlinuz-4.14.8-300.fc27.x86_64
# grubby --default-index
1
# shutdown -r now
$ ./Run -i 1
以下、結果となります。
Linux gns3-iouvm 4.14.11-300.fc27.x86_64 #1 SMP Wed Jan 3 13:52:28 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux
Benchmark Run: 月 1月 08 2018 16:19:46 - 16:26:35
8 CPUs in system; running 1 parallel copy of tests
Dhrystone 2 using register variables 40574757.7 lps (10.0 s, 1 samples)
Double-Precision Whetstone 4203.7 MWIPS (11.9 s, 1 samples)
Execl Throughput 4855.8 lps (29.8 s, 1 samples)
File Copy 1024 bufsize 2000 maxblocks 975107.0 KBps (30.0 s, 1 samples)
File Copy 256 bufsize 500 maxblocks 260045.0 KBps (30.0 s, 1 samples)
File Copy 4096 bufsize 8000 maxblocks 2497555.0 KBps (30.0 s, 1 samples)
Pipe Throughput 1395146.1 lps (10.0 s, 1 samples)
Pipe-based Context Switching 222524.1 lps (10.0 s, 1 samples)
Process Creation 11913.3 lps (30.0 s, 1 samples)
Shell Scripts (1 concurrent) 7391.3 lpm (60.0 s, 1 samples)
Shell Scripts (8 concurrent) 3107.5 lpm (60.0 s, 1 samples)
System Call Overhead 1022589.9 lps (10.0 s, 1 samples)
System Benchmarks Index Values BASELINE RESULT INDEX
Dhrystone 2 using register variables 116700.0 40574757.7 3476.8
Double-Precision Whetstone 55.0 4203.7 764.3
Execl Throughput 43.0 4855.8 1129.3
File Copy 1024 bufsize 2000 maxblocks 3960.0 975107.0 2462.4
File Copy 256 bufsize 500 maxblocks 1655.0 260045.0 1571.3
File Copy 4096 bufsize 8000 maxblocks 5800.0 2497555.0 4306.1
Pipe Throughput 12440.0 1395146.1 1121.5
Pipe-based Context Switching 4000.0 222524.1 556.3
Process Creation 126.0 11913.3 945.5
Shell Scripts (1 concurrent) 42.4 7391.3 1743.2
Shell Scripts (8 concurrent) 6.0 3107.5 5179.1
System Call Overhead 15000.0 1022589.9 681.7
========
System Benchmarks Index Score 1542.6
------------------------------------------------------------------------
Benchmark Run: 月 1月 08 2018 16:26:35 - 16:33:24
8 CPUs in system; running 8 parallel copies of tests
Dhrystone 2 using register variables 185141692.8 lps (10.0 s, 1 samples)
Double-Precision Whetstone 32704.8 MWIPS (10.0 s, 1 samples)
Execl Throughput 21620.1 lps (29.3 s, 1 samples)
File Copy 1024 bufsize 2000 maxblocks 1232533.0 KBps (30.0 s, 1 samples)
File Copy 256 bufsize 500 maxblocks 324473.0 KBps (30.0 s, 1 samples)
File Copy 4096 bufsize 8000 maxblocks 3280739.0 KBps (30.0 s, 1 samples)
Pipe Throughput 7777059.3 lps (10.0 s, 1 samples)
Pipe-based Context Switching 1677078.9 lps (10.0 s, 1 samples)
Process Creation 61386.3 lps (30.0 s, 1 samples)
Shell Scripts (1 concurrent) 25670.6 lpm (60.0 s, 1 samples)
Shell Scripts (8 concurrent) 4065.0 lpm (60.0 s, 1 samples)
System Call Overhead 6014480.6 lps (10.0 s, 1 samples)
System Benchmarks Index Values BASELINE RESULT INDEX
Dhrystone 2 using register variables 116700.0 185141692.8 15864.8
Double-Precision Whetstone 55.0 32704.8 5946.3
Execl Throughput 43.0 21620.1 5027.9
File Copy 1024 bufsize 2000 maxblocks 3960.0 1232533.0 3112.5
File Copy 256 bufsize 500 maxblocks 1655.0 324473.0 1960.6
File Copy 4096 bufsize 8000 maxblocks 5800.0 3280739.0 5656.4
Pipe Throughput 12440.0 7777059.3 6251.7
Pipe-based Context Switching 4000.0 1677078.9 4192.7
Process Creation 126.0 61386.3 4871.9
Shell Scripts (1 concurrent) 42.4 25670.6 6054.4
Shell Scripts (8 concurrent) 6.0 4065.0 6774.9
System Call Overhead 15000.0 6014480.6 4009.7
========
System Benchmarks Index Score 5144.8
---------------------------------------------------------
Linux gns3-iouvm 4.14.8-300.fc27.x86_64 #1 SMP Wed Dec 20 19:00:18 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Benchmark Run: 月 1月 08 2018 17:03:43 - 17:10:32
8 CPUs in system; running 1 parallel copy of tests
Dhrystone 2 using register variables 38787410.5 lps (10.0 s, 1 samples)
Double-Precision Whetstone 4715.0 MWIPS (9.4 s, 1 samples)
Execl Throughput 5127.7 lps (29.4 s, 1 samples)
File Copy 1024 bufsize 2000 maxblocks 1234002.0 KBps (30.0 s, 1 samples)
File Copy 256 bufsize 500 maxblocks 367602.0 KBps (30.0 s, 1 samples)
File Copy 4096 bufsize 8000 maxblocks 2770317.0 KBps (30.0 s, 1 samples)
Pipe Throughput 2403210.0 lps (10.0 s, 1 samples)
Pipe-based Context Switching 246422.0 lps (10.1 s, 1 samples)
Process Creation 13904.1 lps (30.0 s, 1 samples)
Shell Scripts (1 concurrent) 8324.7 lpm (60.0 s, 1 samples)
Shell Scripts (8 concurrent) 3414.6 lpm (60.0 s, 1 samples)
System Call Overhead 3717750.5 lps (10.1 s, 1 samples)
System Benchmarks Index Values BASELINE RESULT INDEX
Dhrystone 2 using register variables 116700.0 38787410.5 3323.7
Double-Precision Whetstone 55.0 4715.0 857.3
Execl Throughput 43.0 5127.7 1192.5
File Copy 1024 bufsize 2000 maxblocks 3960.0 1234002.0 3116.2
File Copy 256 bufsize 500 maxblocks 1655.0 367602.0 2221.2
File Copy 4096 bufsize 8000 maxblocks 5800.0 2770317.0 4776.4
Pipe Throughput 12440.0 2403210.0 1931.8
Pipe-based Context Switching 4000.0 246422.0 616.1
Process Creation 126.0 13904.1 1103.5
Shell Scripts (1 concurrent) 42.4 8324.7 1963.4
Shell Scripts (8 concurrent) 6.0 3414.6 5691.1
System Call Overhead 15000.0 3717750.5 2478.5
========
System Benchmarks Index Score 1999.6
------------------------------------------------------------------------
Benchmark Run: 月 1月 08 2018 17:10:32 - 17:17:22
8 CPUs in system; running 8 parallel copies of tests
Dhrystone 2 using register variables 194870992.0 lps (10.0 s, 1 samples)
Double-Precision Whetstone 32731.0 MWIPS (10.0 s, 1 samples)
Execl Throughput 24319.6 lps (29.4 s, 1 samples)
File Copy 1024 bufsize 2000 maxblocks 1240097.0 KBps (30.0 s, 1 samples)
File Copy 256 bufsize 500 maxblocks 327270.0 KBps (30.0 s, 1 samples)
File Copy 4096 bufsize 8000 maxblocks 3724579.0 KBps (30.0 s, 1 samples)
Pipe Throughput 10678393.5 lps (10.0 s, 1 samples)
Pipe-based Context Switching 1837741.4 lps (10.0 s, 1 samples)
Process Creation 67289.8 lps (30.0 s, 1 samples)
Shell Scripts (1 concurrent) 29604.7 lpm (60.0 s, 1 samples)
Shell Scripts (8 concurrent) 4406.6 lpm (60.1 s, 1 samples)
System Call Overhead 8087883.0 lps (10.0 s, 1 samples)
System Benchmarks Index Values BASELINE RESULT INDEX
Dhrystone 2 using register variables 116700.0 194870992.0 16698.5
Double-Precision Whetstone 55.0 32731.0 5951.1
Execl Throughput 43.0 24319.6 5655.7
File Copy 1024 bufsize 2000 maxblocks 3960.0 1240097.0 3131.6
File Copy 256 bufsize 500 maxblocks 1655.0 327270.0 1977.5
File Copy 4096 bufsize 8000 maxblocks 5800.0 3724579.0 6421.7
Pipe Throughput 12440.0 10678393.5 8583.9
Pipe-based Context Switching 4000.0 1837741.4 4594.4
Process Creation 126.0 67289.8 5340.5
Shell Scripts (1 concurrent) 42.4 29604.7 6982.2
Shell Scripts (8 concurrent) 6.0 4406.6 7344.4
System Call Overhead 15000.0 8087883.0 5391.9
========
System Benchmarks Index Score 5748.3
Pipe-based Context Switching で、約 10% の低下、総じて、10 〜 20 % は低下している感じですかね。
(参考)
https://docs.fedoraproject.org/f27/system-administrators-guide/kernel-module-driver-configuration/Working_with_the_GRUB_2_Boot_Loader.html
https://qiita.com/tenn25/items/6fb0d846b28a06bec204
Switch の SVI インターフェースの down down を解決する
SWITCH の設定をしていて、SVI インターフェースが up しない、という事がよくあると思います。
この理由について、考え、解決します。
今、以下のようなトポロジを考えます。

SW1(config)#vlan 111
SW1(config-vlan)#
SW1#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Et0/0, Et0/1, Et0/2, Et0/3
Et1/0, Et1/1, Et1/2, Et1/3
Et2/0, Et2/1, Et2/2, Et2/3
Et3/0, Et3/1, Et3/2, Et3/3
111 VLAN0111 active
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsupVLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
111 enet 100111 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
SW1(config)#int vlan 111
SW1(config-if)#ip address 1.1.1.111 255.255.255.0
SW1(config-if)#no shut
SW1#show ip int brief
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 unassigned YES unset up up
Ethernet0/1 unassigned YES unset up up
Ethernet0/2 unassigned YES unset up up
Ethernet0/3 unassigned YES unset up up
...(snip)...
Vlan1 unassigned YES unset administratively down down
Vlan111 1.1.1.111 YES NVRAM down down
Vlan 111 のインターフェースを no shut したはずなのに、Status が down、Protocol が down のままです。
これは、Vlan 111 に接続されているインターフェースがないからです。
SW1(config)#int range e0/0 -3
SW1(config-if-range)#switchport access vlan
SW1(config-if-range)#switchport access vlan 111
*Dec 16 09:53:01.364: %LINK-3-UPDOWN: Interface Vlan111, changed state to up
*Dec 16 09:53:02.364: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan111, changed state to up
お、アップしたようです。
SW1#show ip int bri
Interface IP-Address OK? Method Status Protocol
Ethernet0/0 unassigned YES unset up up
Ethernet0/1 unassigned YES unset up up
Ethernet0/2 unassigned YES unset up up
Ethernet0/3 unassigned YES unset up up
...(snip)...
Vlan1 unassigned YES unset up up
Vlan111 1.1.1.111 YES NVRAM up up
アップしました。
結局、当該 Vlan にアクセスするポートが 1つ以上ないと、SVI インターフェースは、アップしない、ということのようです。
portfast, uplinkfast, backbonefastその2
このセクションでは、802.1d スパニングツリーのトポロジの変更プロセスとSTPタイマーへの影響を確認します。
SW3 の fa1/0 の portfast 機能を無効にしなさい。
--------
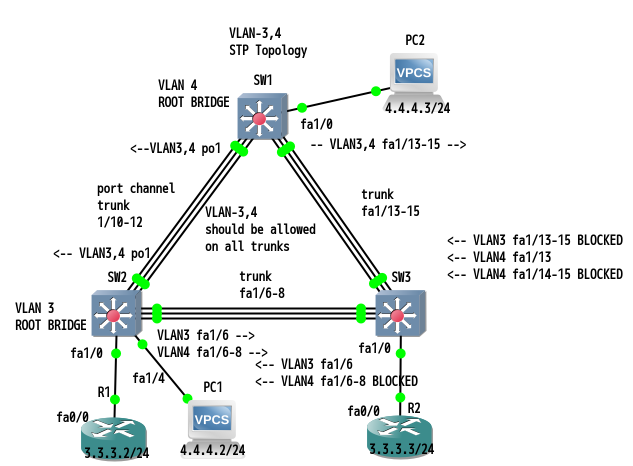
まずは、現在の設定を確認します。
SW3#show spanning-tree active | begin FastEthernet1/0
Port 41 (FastEthernet1/0) of VLAN3 is forwarding
Port path cost 19, Port priority 128, Port Identifier 128.41.
Designated root has priority 8192, address c207.153c.0000
Designated bridge has priority 32768, address c201.1621.0000
Designated port id is 128.41, designated path cost 18
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 4694, received 0
The port is in the portfast mode <--------portfast が有効になっています。
では、fa1/0 上で portfast を無効にします。
SW3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW3(config)#interface fa1/0
SW3(config-if)#no spanning-tree portfast
確認します。
SW3#show spanning-tree interface fa1/0 portfast
VLAN3 disabled
SW3 上で、portfast を無効にしました。portfast を無効にしたので、learning, forwarding, blocking になり、スパニングツリー変更のお知らせを、ルートブリッジ
に送信するはずです。
それを確認します。
SW3 で、デバッグモードにします。そのうえで、fa1/0 をシャットダウンして、トポロジの変更を見てみます。また、fa1/0 を再度有効に(no shut)してみます。
SW3#debug spanning-tree events
Spanning Tree event debugging is on
SW3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW3(config)#interface fa1/0
SW3(config-if)#shutdown
SW3(config-if)#
*Mar 1 03:24:37.159: STP: VLAN3 sent Topology Change Notice on Fa1/15
*Mar 1 03:24:37.159: STP: VLAN3 Fa1/0 -> blocking
SW3(config-if)#
*Mar 1 03:24:39.171: %LINK-5-CHANGED: Interface FastEthernet1/0, changed state to administratively down
*Mar 1 03:24:40.171: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to down
SW3(config-if)#no shutdown
SW3(config-if)#
*Mar 1 03:24:46.759: STP: VLAN3 Fa1/0 -> listening
SW3(config-if)#
*Mar 1 03:24:49.735: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to up
SW3(config-if)#
*Mar 1 03:25:01.767: STP: VLAN3 Fa1/0 -> learning
SW3(config-if)#
*Mar 1 03:25:16.779: STP: VLAN3 sent Topology Change Notice on Fa1/15
*Mar 1 03:25:16.779: STP: VLAN3 Fa1/0 -> forwarding
では、portfast を有効にして、もう一度やってみます。
SW3(config-if)#spanning-tree portfast
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/0 but will only
have effect when the interface is in a non-trunking mode.
SW3#show spanning-tree active | begin FastEthernet1/0
from FastEthernet1/0
Times: hold 1, topology change 35, notification 2
hello 2, max age 20, forward delay 15
Timers: hello 0, topology change 0, notification 0, aging 300
Port 41 (FastEthernet1/0) of VLAN3 is forwarding
Port path cost 19, Port priority 128, Port Identifier 128.41.
Designated root has priority 8192, address c207.153c.0000
Designated bridge has priority 32768, address c201.1621.0000
Designated port id is 128.41, designated path cost 18
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 129, received 0
The port is in the portfast mode
SW3(config)#interface fa1/0
SW3(config-if)#
SW3(config-if)#
SW3(config-if)#
SW3(config-if)#shutdown
SW3(config-if)#
*Mar 1 03:30:18.591: STP: VLAN3 Fa1/0 -> blocking
SW3(config-if)#
*Mar 1 03:30:20.535: %LINK-5-CHANGED: Interface FastEthernet1/0, changed state to administratively down
*Mar 1 03:30:21.535: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to down
SW3(config-if)#no shutdown
SW3(config-if)#
*Mar 1 03:30:33.683: STP: VLAN3 Fa1/0 ->jump to forwarding from blocking
SW3(config-if)#
*Mar 1 03:30:36.639: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to up
SW3(config-if)#end
SW3#show s
*Mar 1 03:32:04.683: %SYS-5-CONFIG_I: Configured from console by console
SW3#show spanning-tree vlan 3 brief
VLAN3
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c207.153c.0000
Cost 18
Port 56 (FastEthernet1/15)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c201.1621.0000
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/0 128.41 128 19 FWD 18 32768 c201.1621.0000 128.41
...
デバッグモードを元に戻します。
SW3#undebug all
お疲れさまです。次回をお楽しみに。
portfast, uplinkfast, backbonefast
このタスクでは、STPトポロジにおける速いコンバージェンスを実現するオプションのスパニングツリー機能を設定する。
それぞれのスイッチ上のただ一つのスパニングツリー命令により、どんなアクセススイッチポートがオンラインになる時、スパニングツリーのリスニング、ラーニング状態を省略して、
直接フォワーディンぐ状態になること。
スイッチ2上のただ一つのスパニングツリー命令により、 ルートポートが物理的に失われた場合、1、2秒で新なルートポートが回復されること。
それぞれのスイッチ上のただ一つのスパニングツリー命令により、指定ポートの関節リンクが失われた時に、およそ 30秒でスパニングツリートポロジのコンバージェンスが回復すること。
上記をすべて検証すること。

GNS3 では、spanning-tree uplinkfast と、spanning-tree backbonefast は有効だが、spanning-tree portfast は、
それぞれのインタフェースにおいて有効にする必要があります。
SW2#conf t
*Mar 1 01:36:08.175: %SYS-5-CONFIG_I: Configured from console by console
SW2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW2(config)#int range fa1/0 - 15 , po1
SW2(config-if-range)#spann
SW2(config-if-range)#spanning-tree ?
cost Change an interface's spanning tree path cost
port-priority Change an interface's spanning tree priority
portfast Enable an interface to move directly to forwarding on link up
vlan VLAN Switch Spanning Tree
SW2(config-if-range)#spanning-tree portfast
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/0 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/1 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/2 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/3 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/4 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/5 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/6 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/7 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/8 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/9 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/10 but will only
have effect when the interface
*Mar 1 01:36:47.411: %EC-5-UNBUNDLE: Interface Fa1/10 left the port-channel Po1
*Mar 1 01:36:47.483: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:47.487: %SPANTREE_FAST-7-PORT_FWD_UPLINK: VLAN1 Port-channel1 moved to Forwarding (UplinkFast).
*Mar 1 01:36:47.535: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
*Mar 1 01:36:47.535: %EC-5-BUNDLE: Interface Fa1/10 joined port-channel Po1
*Mar 1 01:36:47.535: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:47.563: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/11 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/12 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has
*Mar 1 01:36:52.791: %EC-5-UNBUNDLE: Interface Fa1/11 left the port-channel Po1
*Mar 1 01:36:52.831: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:52.831: %SPANTREE_FAST-7-PORT_FWD_UPLINK: VLAN1 Port-channel1 moved to Forwarding (UplinkFast).
*Mar 1 01:36:52.831: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
*Mar 1 01:36:52.831: %EC-5-BUNDLE: Interface Fa1/11 joined port-channel Po1
*Mar 1 01:36:52.831: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:52.831: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
*Mar 1 01:36:52.883: %EC-5-UNBUNDLE: Interface Fa1/12 left the port-channel Po1
*Mar 1 01:36:52.883: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:52.883: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
*Mar 1 01:36:52.883: %EC-5-BUNDLE: Interface Fa1/12 joined port-channel Po1
*Mar 1 01:36:52.923: STP FAST: UPLINKFAST: make_forwarding on VLAN1 Port-channel1 root port id new: 129.65 prev: 128.47
*Mar 1 01:36:52.935: STP FAST: UPLINKFAST: make_forwarding on VLAN1 FastEthernet1/6 root port id new: 128.47 prev: 129.65
been configured on FastEthernet1/13 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/14 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/15 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on Port-channel1 but will only
have effect when the interface is in a non-trunking mode.
SW1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface range fa1/0 - 15 , po1
SW1(config-if-range)#spanning-tree portfast
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/0 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/1 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/2 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/3 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/4 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/5 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/6 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/7 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/8 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/9 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/10 but will only
have effect when the interface is in a non-tru
*Mar 1 01:40:00.591: %EC-5-UNBUNDLE: Interface Fa1/10 left the port-channel Po1
*Mar 1 01:40:00.687: %EC-5-BUNDLE: Interface Fa1/10 joined port-channel Po1nking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/11 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/12 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast
*Mar 1 01:40:03.927: %EC-5-UNBUNDLE: Interface Fa1/11 left the port-channel Po1
*Mar 1 01:40:04.027: %EC-5-BUNDLE: Interface Fa1/11 joined port-channel Po1
*Mar 1 01:40:04.027: %EC-5-UNBUNDLE: Interface Fa1/12 left the port-channel Po1
*Mar 1 01:40:04.027: %EC-5-BUNDLE: Interface Fa1/12 joined port-channel Po1 has been configured on FastEthernet1/13 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/14 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/15 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on Port-channel1 but will only
have effect when the interface is in a non-trunking mode.
SW3#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW3(config)#int range fa1/0 - 15
SW3(config-if-range)#spanning-tree portfast
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/0 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/1 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/2 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/3 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/4 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/5 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/6 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/7 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/8 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/9 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/10 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/11 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/12 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/13 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/14 but will only
have effect when the interface is in a non-trunking mode.
%Warning: portfast should only be enabled on ports connected to a single host.
Connecting hubs, concentrators, switches, bridges, etc.to this interface
when portfast is enabled, can cause temporary spanning tree loops.
Use with CAUTION
%Portfast has been configured on FastEthernet1/15 but will only
have effect when the interface is in a non-trunking mode.
ーーーーーーーーーーーーーーーーーーーーーー
SW3# show spanning-tree active
...(snip)...
Port 41 (FastEthernet1/0) of VLAN3 is forwarding
Port path cost 19, Port priority 128, Port Identifier 128.41.
Designated root has priority 8192, address c207.153c.0000
Designated bridge has priority 32768, address c201.1621.0000
Designated port id is 128.41, designated path cost 18
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 3196, received 0
The port is in the portfast mode <---portfast モードになっている
SW2# show spanning-tree active
...(snip)...
Port 41 (FastEthernet1/0) of VLAN3 is forwarding
Port path cost 19, Port priority 128, Port Identifier 128.41.
Designated root has priority 8192, address c207.153c.0000
Designated bridge has priority 8192, address c207.153c.0000
Designated port id is 128.41, designated path cost 0
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 3376, received 0
The port is in the portfast mode
Port 45 (FastEthernet1/4) of VLAN4 is forwarding
Port path cost 3019, Port priority 128, Port Identifier 128.45.
Designated root has priority 8192, address c206.152d.0000
Designated bridge has priority 49152, address c207.153c.0001
Designated port id is 128.45, designated path cost 37
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 3391, received 0
The port is in the portfast mode
SW1# show spanning-tree active
...(snip)...
Port 41 (FastEthernet1/0) of VLAN4 is forwarding
Port path cost 19, Port priority 128, Port Identifier 128.41.
Designated root has priority 8192, address c206.152d.0000
Designated bridge has priority 8192, address c206.152d.0000
Designated port id is 128.41, designated path cost 0
Timers: message age 0, forward delay 0, hold 0
Number of transitions to forwarding state: 1
BPDU: sent 3539, received 0
The port is in the portfast mode
SW2#show spanning-tree summary
Root bridge for: VLAN3.
PortFast BPDU Guard is disabled
UplinkFast is enabled <------------------uplinkfast が有効になっている
BackboneFast is disabled
Name Blocking Listening Learning Forwarding STP Active
-------------------- -------- --------- -------- ---------- ----------
VLAN1 3 0 0 1 4
VLAN3 0 0 0 5 5
VLAN4 3 0 0 2 5
-------------------- -------- --------- -------- ---------- ----------
3 VLANs 6 0 0 8 14
Station update rate set to 150 packets/sec.
UplinkFast statistics
-----------------------
Number of transitions via uplinkFast (all VLANs) : 18
Number of proxy multicast addresses transmitted (all VLANs) : 0
SW2#show spanning-tree uplinkfast
UplinkFast is enabled
Station update rate set to 150 packets/sec.
UplinkFast statistics
-----------------------
Number of transitions via uplinkFast (all VLANs) : 18
Number of proxy multicast addresses transmitted (all VLANs) : 0
Name Interface List
-------------------- ------------------------------------
VLAN1 Fa1/6(fwd), Fa1/7, Fa1/8, Po1
VLAN3
VLAN4 Fa1/8(fwd), Fa1/6, Fa1/7, Po1
SW1#show spanning-tree summary
Root bridge for: VLAN4.
PortFast BPDU Guard is disabled
UplinkFast is disabled
BackboneFast is enabled <----------------------backbonefast が有効になっている
Name Blocking Listening Learning Forwarding STP Active
-------------------- -------- --------- -------- ---------- ----------
VLAN1 2 0 0 2 4
VLAN3 0 0 0 4 4
VLAN4 0 0 0 5 5
-------------------- -------- --------- -------- ---------- ----------
3 VLANs 2 0 0 11 13
BackboneFast statistics
-----------------------
Number of transition via backboneFast (all VLANs) : 0
Number of inferior BPDUs received (all VLANs) : 0
Number of RLQ request PDUs received (all VLANs) : 0
Number of RLQ response PDUs received (all VLANs) : 0
Number of RLQ request PDUs sent (all VLANs) : 0
Number of RLQ response PDUs sent (all VLANs) : 0
SW1#show spanning-tree backbonefast
BackboneFast is enabled
BackboneFast statistics
-----------------------
Number of transition via backboneFast (all VLANs) : 0
Number of inferior BPDUs received (all VLANs) : 0
Number of RLQ request PDUs received (all VLANs) : 0
Number of RLQ response PDUs received (all VLANs) : 0
Number of RLQ request PDUs sent (all VLANs) : 0
Number of RLQ response PDUs sent (all VLANs) : 0
お疲れさまです。次回をお楽しみに。
STPトポロジ-3(パスコスト変更による通信経路の変更2)
このタスクでは、802.1d PVST Spanning-Tree コマンドにより、VLAN-4 の通信経路を操ります。
このタスクが完遂されれば、PC1 から PC2 への VLAN-4 の ping による通信経路は、PC1-->SW2-->SW3-->SW1-->PC2 となる。
ただ一つのスイッチ上の spanning-tree コマンドが、SW3 が、fa1/14をVLAN-4 のルートポートとすることを選択するようにしなさい。
どのスイッチ上のポートコストも変更してはならない。
どのインタフェースも閉鎖してはならない。
ルートブリッジを変更してはならない。
2つ以上のコマンドを使用して、SW2 が fa1/8 を、VLAN-4 のためのルートポートとなるようにせよ。
どのインタフェースも閉鎖してはならない。
ルートブリッジを変更してはならない。
このタスクが完遂されたら、VLAN-4 のスパニングツリーは、PC1-->SW2(fa1/8)-->SW3(fa1/8)-->SW3(fa1/14)-->SW1(fa1/14)-->PC2 となるようになる。
トポロジは、以下を使います。

--------
まず、それぞれのスイッチで、VLAN-4 のスパニングツリーを確認しておく。
SW1#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
This bridge is the root
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 8192
Address c206.152d.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/0 128.41 128 19 FWD 0 8192 c206.152d.0002 128.41
FastEthernet1/13 128.54 128 19 FWD 0 8192 c206.152d.0002 128.54
FastEthernet1/14 128.55 128 19 FWD 0 8192 c206.152d.0002 128.55
FastEthernet1/15 128.56 128 19 FWD 0 8192 c206.152d.0002 128.56
Port-channel1 129.65 128 9 FWD 0 8192 c206.152d.0002 129.65
SW2#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 9
Port 321 (Port-channel1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c207.153c.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/4 128.45 128 19 FWD 9 32768 c207.153c.0002 128.45
FastEthernet1/6 128.47 128 19 FWD 9 32768 c207.153c.0002 128.47
FastEthernet1/7 128.48 128 19 FWD 9 32768 c207.153c.0002 128.48
FastEthernet1/8 128.49 128 19 FWD 9 32768 c207.153c.0002 128.49
Port-channel1 129.65 128 9 FWD 0 8192 c206.152d.0002 129.65
SW3#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 19
Port 54 (FastEthernet1/13)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c201.1621.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/6 128.47 128 19 BLK 9 32768 c207.153c.0002 128.47
FastEthernet1/7 128.48 128 19 BLK 9 32768 c207.153c.0002 128.48
FastEthernet1/8 128.49 128 19 BLK 9 32768 c207.153c.0002 128.49
FastEthernet1/13 128.54 128 19 FWD 0 8192 c206.152d.0002 128.54
FastEthernet1/14 128.55 128 19 BLK 0 8192 c206.152d.0002 128.55
FastEthernet1/15 128.56 128 19 BLK 0 8192 c206.152d.0002 128.56
ここで、SW3 の fa1/14 はブロッキングであり、fa1/13 がフォーワディングとなっている。これを、fa1/14 がフォーワディングになるようにするには、
ポートプライオリティを下げればよいと考えられる。ポートプライオリティは、16の倍数で増える。なので、128 -16 の、112 にすればよいと考える。
ここで、SW3 の peer で実行する必要がある。したがって、SW1 上で、以下のコマンドを発行する。
SW1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface fa1/14
SW1(config-if)#end
SW1#d
*Mar 1 09:36:00.577: %SYS-5-CONFIG_I: Configured from console by console
SW1#debug spanning-tree eve
SW1#debug spanning-tree events
Spanning Tree event debugging is on
SW1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface fa1/14
SW1(config-if)#spanning-tree vlan 4 port-pri
SW1(config-if)#spanning-tree vlan 4 port-priority 112
SW1(config-if)#
*Mar 1 09:36:43.745: STP: VLAN4 Topology Change rcvd on Fa1/14
SW1(config-if)#
*Mar 1 09:37:13.781: STP: VLAN4 Topology Change rcvd on Fa1/14
SW1#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
This bridge is the root
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 8192
Address c206.152d.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/0 128.41 128 19 FWD 0 8192 c206.152d.0002 128.41
FastEthernet1/13 128.54 128 19 FWD 0 8192 c206.152d.0002 128.54
FastEthernet1/14 112.55 112 19 FWD 0 8192 c206.152d.0002 112.55
FastEthernet1/15 128.56 128 19 FWD 0 8192 c206.152d.0002 128.56
Port-channel1 129.65 128 9 FWD 0 8192 c206.152d.0002 129.65
SW3 の fa1/14 がフォワードとなってくれたか確認する。
(省略)
なってくれた。
次に、SW2-SW1 間のコストを上げてみる。今、SW2-SW1 間はポートチャネルになっており、そのパスコストは 9 である。
このパスを通させたくないので、SW2-SW3-SW1 とさせるには、そのパスコスト 19 + 19 = 38 より大きい 39 とすれば
よさそうである。
SW2#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 9
Port 321 (Port-channel1)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c207.153c.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/4 128.45 128 19 FWD 9 32768 c207.153c.0002 128.45
FastEthernet1/6 128.47 128 19 FWD 9 32768 c207.153c.0002 128.47
FastEthernet1/7 128.48 128 19 FWD 9 32768 c207.153c.0002 128.48
FastEthernet1/8 128.49 128 19 FWD 9 32768 c207.153c.0002 128.49
Port-channel1 129.65 128 9 FWD 0 8192 c206.152d.0002 129.65
SW2 上で、以下のコマンドを発行する。
SW2#debug spanning-tree events
Spanning Tree event debugging is on
SW2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW2(config)#interface port
SW2(config)#interface port-channel 1
SW2(config-if)#spanning-tree vlan 4 cost 39
SW2(config-if)#
*Mar 1 09:13:24.681: STP: VLAN4 new root port Fa1/6, cost 38
*Mar 1 09:13:24.685: STP: VLAN4 sent Topology Change Notice on Fa1/6
*Mar 1 09:13:24.729: STP: VLAN4 Po1 -> blocking
*Mar 1 09:13:24.729: STP: VLAN4 Fa1/7 -> blocking
*Mar 1 09:13:24.781: STP: VLAN4 Fa1/8 -> blocking
SW2#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 38
Port 47 (FastEthernet1/6)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c207.153c.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/4 128.45 128 19 FWD 38 32768 c207.153c.0002 128.45
FastEthernet1/6 128.47 128 19 FWD 19 32768 c201.1621.0002 128.47
FastEthernet1/7 128.48 128 19 BLK 19 32768 c201.1621.0002 128.48
FastEthernet1/8 128.49 128 19 BLK 19 32768 c201.1621.0002 128.49
Port-channel1 129.65 128 39 BLK 0 8192 c206.152d.0002 129.65
SW3 では、以下のようになった。
SW3#
*Mar 1 09:13:23.941: STP: VLAN4 Fa1/6 -> listening
*Mar 1 09:13:23.985: STP: VLAN4 Fa1/7 -> listening
*Mar 1 09:13:24.041: STP: VLAN4 Fa1/8 -> listening
*Mar 1 09:13:24.877: STP: VLAN4 Topology Change rcvd on Fa1/6
*Mar 1 09:13:24.877: STP: VLAN4 sent Topology Change Notice on Fa1/13
SW3#
*Mar 1 09:13:38.949: STP: VLAN4 Fa1/6 -> learning
*Mar 1 09:13:38.985: STP: VLAN4 Fa1/7 -> learning
*Mar 1 09:13:39.049: STP: VLAN4 Fa1/8 -> learning
SW3#
*Mar 1 09:13:53.957: STP: VLAN4 sent Topology Change Notice on Fa1/13
*Mar 1 09:13:53.957: STP: VLAN4 Fa1/6 -> forwarding
*Mar 1 09:13:53.997: STP: VLAN4 sent Topology Change Notice on Fa1/13
*Mar 1 09:13:53.997: STP: VLAN4 Fa1/7 -> forwarding
*Mar 1 09:13:54.057: STP: VLAN4 Fa1/8 -> forwarding
最後に、SW2 上で fa1/8 がフォワードになるようにします。
SW2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW2(config)#interface fa1/8
SW2(config-if)#spanning-tree vlan 4 cost 18
SW2(config-if)#
*Mar 1 09:31:42.257: STP: VLAN4 new root port Fa1/8, cost 37
*Mar 1 09:31:42.257: STP: VLAN4 sent Topology Change Notice on Fa1/8
*Mar 1 09:31:42.305: STP: VLAN4 Fa1/6 -> blocking
*Mar 1 09:31:42.305: STP: VLAN4 Fa1/8 -> listening
SW2(config-if)#
*Mar 1 09:31:57.313: STP: VLAN4 Fa1/8 -> learning
SW2(config-if)#
*Mar 1 09:32:12.321: STP: VLAN4 sent Topology Change Notice on Fa1/8
*Mar 1 09:32:12.325: STP: VLAN4 Fa1/8 -> forwarding
SW2#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 37
Port 49 (FastEthernet1/8)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c207.153c.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/4 128.45 128 19 FWD 37 32768 c207.153c.0002 128.45
FastEthernet1/6 128.47 128 19 BLK 19 32768 c201.1621.0002 128.47
FastEthernet1/7 128.48 128 19 BLK 19 32768 c201.1621.0002 128.48
FastEthernet1/8 128.49 128 18 FWD 19 32768 c201.1621.0002 128.49
Port-channel1 129.65 128 39 BLK 0 8192 c206.152d.0002 129.65
SW3、SW1 の VLAN-4 のスパニングツリーも、もう一度確認する。
SW3#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
Cost 19
Port 55 (FastEthernet1/14)
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 32768
Address c201.1621.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/6 128.47 128 19 FWD 19 32768 c201.1621.0002 128.47
FastEthernet1/7 128.48 128 19 FWD 19 32768 c201.1621.0002 128.48
FastEthernet1/8 128.49 128 19 FWD 19 32768 c201.1621.0002 128.49
FastEthernet1/13 128.54 128 19 BLK 0 8192 c206.152d.0002 128.54
FastEthernet1/14 128.55 128 19 FWD 0 8192 c206.152d.0002 112.55
FastEthernet1/15 128.56 128 19 BLK 0 8192 c206.152d.0002 128.56
SW1#show spanning-tree vlan 4 brief
VLAN4
Spanning tree enabled protocol ieee
Root ID Priority 8192
Address c206.152d.0002
This bridge is the root
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Bridge ID Priority 8192
Address c206.152d.0002
Hello Time 2 sec Max Age 20 sec Forward Delay 15 sec
Aging Time 300
Interface Designated
Name Port ID Prio Cost Sts Cost Bridge ID Port ID
-------------------- ------- ---- ----- --- ----- -------------------- -------
FastEthernet1/0 128.41 128 19 FWD 0 8192 c206.152d.0002 128.41
FastEthernet1/13 128.54 128 19 FWD 0 8192 c206.152d.0002 128.54
FastEthernet1/14 112.55 112 19 FWD 0 8192 c206.152d.0002 112.55
FastEthernet1/15 128.56 128 19 FWD 0 8192 c206.152d.0002 128.56
Port-channel1 129.65 128 9 FWD 0 8192 c206.152d.0002 129.65
これを読めば、PC1-->SW2(fa1/8)-->SW3(fa1/8)-->SW3(fa1/14)-->SW1(fa1/14)-->PC2 となる
のがわかる。
お疲れさまです。次回をお楽しみに。